Welcome to the third part of this series on “Reverse Engineering android applications”. To read an overview of the series, refer to the serious announcement blog post.
In the previous part, we talked about and performed reverse engineering using Androguard tools like Androaxml, Androsim, Androdd, Apkviewer and Androapkinfo.
Previous part was about android guard tools but continuing with the series, today we will learn and perform reverse engineering using below tools:
- Smali/Baksmali
- Simplify
- Androwarn
- APKAnalyser
1. Smali/Baksmali
What is Smali?
smali/baksmali is an assembler/disassembler for the dex format used by dalvik, Android’s Java VM implementation. The syntax is loosely based on Jasmin’s/dedexer’s syntax, and supports the full functionality of the dex format (annotations, debug info, line info, etc.)
The names “smali” and “baksmali” are the Icelandic equivalents of “assembler” and “disassembler” respectively. (Reference)
IDEs like Eclipse, Android Studio compiles and generate .dex (Dalvik Executable) file from Java source code written by developers in form of a apk file. In order to Reverse Engineer an apk, we need to extract the .dex file, its in unreadable format, so we need to convert .dex to Smali language.
To learn more about Smali, refer this Begineer’s Guide to Smali Coding.
Download Smali and BakSmali jar files from bitbucket.
Lets disassemble .dex or .apk to .smali files
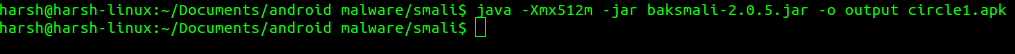
Navigate to the folder containing baksmali jar file and run this command to generate Smali files in output directory.
java -Xmx512m -jar baksmali-x.x.x.jar -o <output directory> <.dex file, or .apk file as input>
In our case it is,
java -Xmx512m -jar baksmali-2.0.5.jar -o output circle1.apk
This will generate Smali files inside output directory specified.
Lets reassemble .smali files to .dex file
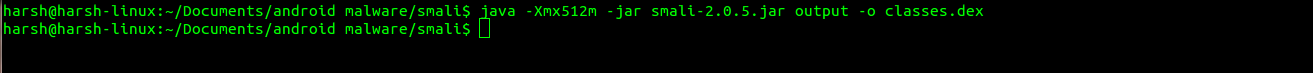
Navigate to the folder containing smali jar file and run this command to reassemble Smali files of output directory to a .dex file.
java -Xmx512m -jar smali-x.x.x.jar <directory containing smali files> -o <output .dex file>
In our case it is,
java -Xmx512m -jar smali-2.0.5.jar output -o classes.dex
2. Using Simplify
Often obfuscation is done to secure and hide code from attackers, thus makes it hard to understand how code works. Sometimes, obfuscation can also be used to hide malicious code. In such case we need a deobfuscator to reverse engineer the file.
Simplify is a code Deobfuscator, that inputs Smali files or folder containing smali files and generates .dex file.
Clone Simplify from Github and build the jar file using ./gradlew shadowJar and navigate to simplify/build/libs folder containing built jar file.
Lets start:
We will use the Smali files generated using Smali/BakSmali as input to Simplify, that will generate dex file as output.
For simplicity I have copied Smali files folder in libs directory.
Now lets run the jar.
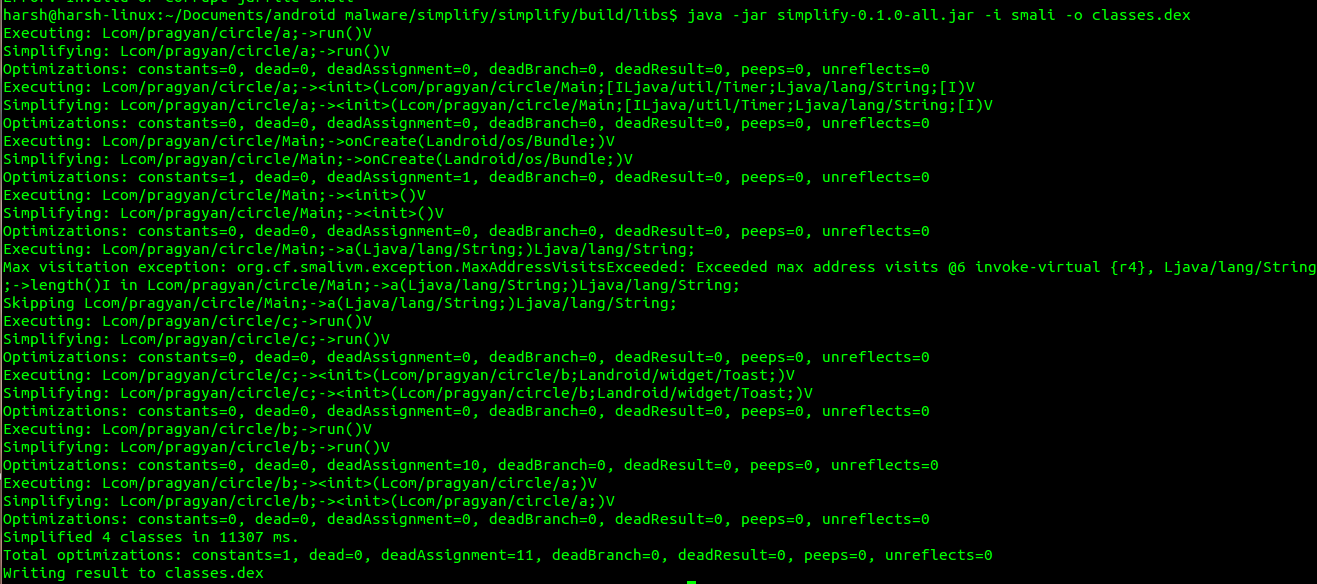
java -jar simplify-0.1.0-all.jar -i <input smali files or folder> -o <output dex file>
In our case:
java -jar simplify-0.1.0-all.jar -i smali -o classes.dex
Classes.dex file is generated, now use Dex2Jar and JD-GUI or any other Java Decompiler to extract contents of dex file.
3. Using Androwarn
Androwarn is a static analysis tool using Smali, that scans Application’s bytecode and generates a report stating if app is malicious or not.
You can get Androwarn from GitHub and prerequisites.
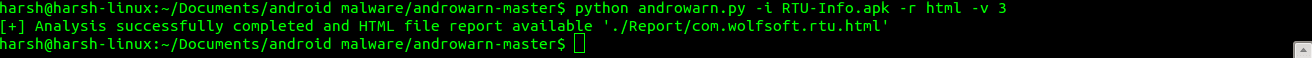
After successful installation of Androwarn, navigate to folder downloaded folder and fire this command in terminal.
python androwarn.py -i <apk_file> -r html -v 3
Html or Text 2 types of report can be generated.
4. Using APKAnalyser
APKAnalyser is a GUI based static code analysis tool and comes with Smali and APKTool included, Paresh has shared about APKAnaLyser in the part 9 of his Lazy Android Developers Series.
In Summary
This bring us to the end of this part. In this part, we explored about the usage of different tools like Smali/Baksmali (assembler/disassembler for the dex format), Simplify (code deobfuscator), Androwarn (a static analysis tool using Smali which scans Application’s bytecode and generates a report stating) and APKAnalyser (which is a GUI based static code analysis tool).
We shall talk about Online tools for Reverse Engineering and Malware Analysis in next part. Till than play with above tools and perform reverse engineering on some of the malicious APKs and check the malicious reports. See you in next part!