Welcome to the fifth part (and probably last part) of this series on “Reverse Engineering android applications”. To read an overview of the series, refer to the serious announcement blog post.
A quick glimpse of all parts:
- Part 1, we talked about Reverse engineering using Androguard tools
- Part 2 was about deep analysis using Androguard
- Part 3 was about other tools that can be used for reverse engineering
- Part 4 was about Online web services for reverse engineering and analysis
Many readers have found installation of Androguard in part 1 as a lengthy process, so here is an easy way of doing it, in this part we will learn about using Santoku Linux, a bootable Linux environment, with set of all tools required for Reverse Engineering, Malware Analysis, Forensics and Security testing.
Download Santoku from here and boot the image in Vmware or Virtualbox. You can refer docs for perfect guide.
First thing to do is check if everything in system is up to date. Open terminal Ctrl + Alt +T and run:
sudo apt-get update and sudo apt-get upgrade
After updating it, we are set to use the system.
1. Using Androguard
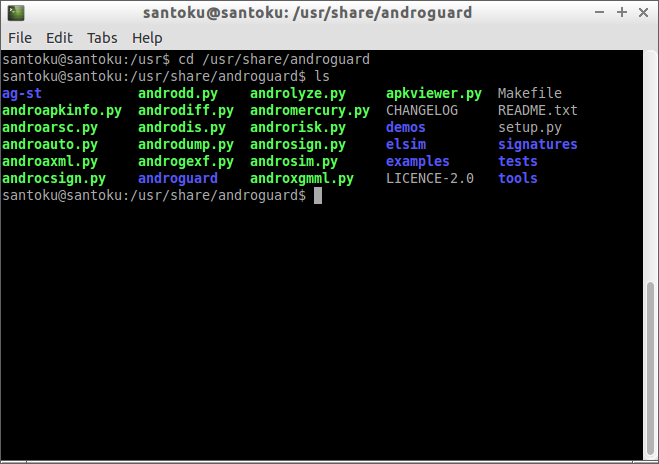
Lets start running Androguard tools that comes pre-installed, to do that open terminal and navigate to navi/usr/share/androguard directory, there you can find all androguard tools as we have discussed in Part 1 and Part 2.
2. Using ApkTool
ApkTool is a 3rd party tool that comes preinstalled with Santoku machine, can be used to decompile and rebuild android binaries from source.
Note: This article does not promote any Piracy or Non-legal uses of using such tools, it for educational and analysis purpose only.
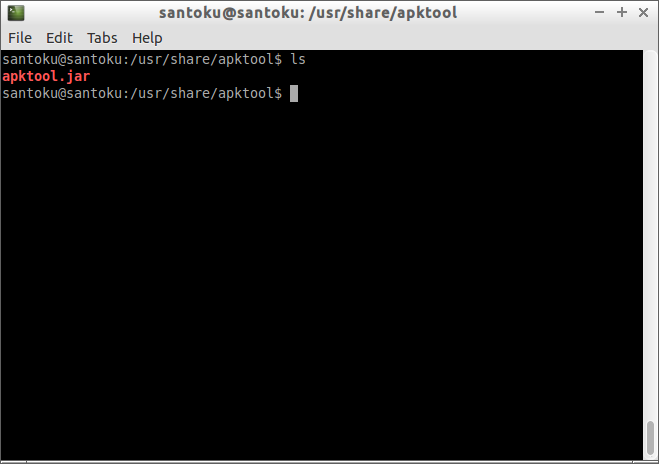
To run ApkTool navigate to /usr/share/apktool/ directory, and you will find a jar file:
Copy the apk which you want to analyze inside this directory or keep it in a handy location.
Run this command:
apktool d
If all goes perfect, and upon navigating to output directory specified at aktool command, we will get a smali folder, We have discussed about Smali/Baksmali in Part 2 of our series.
Santoku is very useful if you don’t want to download and compile each and every tool and want all pre-installed under 1 roof.
3. Procyon Decompiler
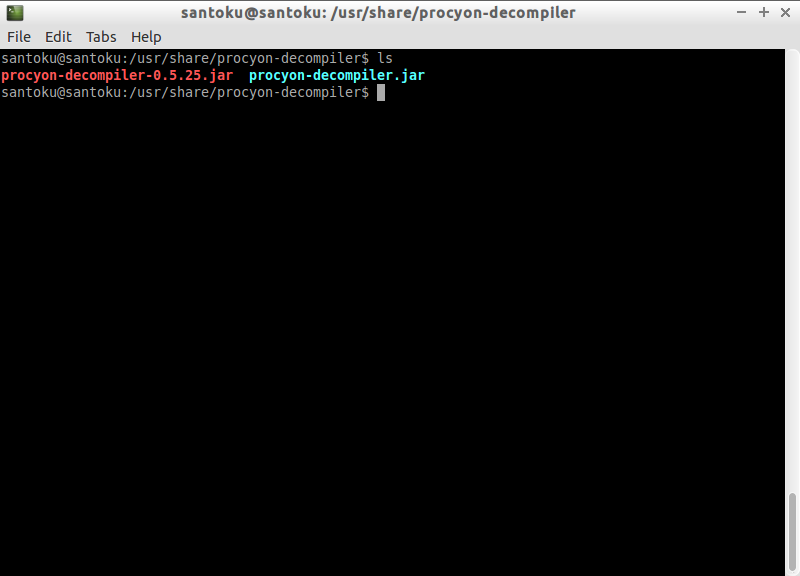
Procyon is one of the actively maintained Java Decompiler, can be forked from Bitbucket easily, but if you are using Sanoku, then procyon comes out of box, simply navigate to /usr/share/procyon-decompiler directory, you can find procyon.jar file there.
Now to decompile a jar run this command:
java -jar procyon-decompiler.jar -jar-o
4. Dex2jar and JD-GUI
Dex2jar and JD-GUI are the famous and widely used tools, these also come out of box in Santoku. Paresh has explained using both in Lazy Android Developer Series, Part 9.
More, Santoku also comes with Forensics tools such as libimobiledevice, a cross platform library to communicate with IOS devices and can be useful in Forensics of IOS Devices. Another useful tool is AFLogical, useful for forensics of Android device, refer this document for more details about using AFLogical to extract device data.
More Santoku, also contains development tools like Android Studio, Eclipse along with SBF Flash and Fastboot.
In Summary
This bring us to the end of this part and probably end of this series. In this part, we talked about performing reverse engineering using virtual machines, as mentioned in the article many of you have found the installation of Androguard described in part 1 somewhat lengthier so this was the article to show you an easy way to do the same job.
Feedback
As said above, probably this would be the last article in this reverse engineering series. This was my first try to publish contents over the web, I am thankful to Paresh for providing a platform and showing a way to share, document stuffs and contribute back to the community.
By looking at feedback received from the readers and community, I would say most of you have enjoyed reading this series. You might have already found some of the parts useful or you may find it useful. Please share your feedback (if any!), it would be a booster for me and may put a force on me to write next series of articles 🙂 Looking forward to hear back from you readers!